Концепция site-to-site VPN и Remote Vpn
Так выглядят 2 основных концепта построения IPSec
2 обобщённые комбинации
Подробное рассмотрение составлящих IPSec
Две разновидности IPSec: AH и ESP. AH не шифрует трафик, потому сразу на помойку, приведено только для общей информации
AH
И, наконец, самое вкусное, ESP
Security Associations
An SA is a basic building block of IPsec. Security associations are maintained within a SA database (SADB), which is established by each device. A VPN has SA entries defining the IPsec encryption parameters as well as SA entries defining the key exchange parameters.
All cryptographic systems, including the Caesar cipher, Vigenere cipher, Enigma machine, to modern encryption algorithms, must deal with key management issues. Diffie-Hellman (DH) is used to create the shared secret key. However, IPsec uses the Internet Key Exchange (IKE) protocol to establish the key exchange process.
Instead of transmitting keys directly across a network, IKE calculates shared keys based on the exchange of a series of data packets. This disables a third party from decrypting the keys even if the third party captured all exchanged data that is used to calculate the keys.
IKE is layered on UDP and uses UDP port 500 to exchange IKE information between the security gateways. UDP port 500 packets must be permitted on any IP interface involved in connecting a security gateway peer.
IKE is defined in RFC 2409. It is a hybrid protocol, combining the Internet Security Association and Key Management Protocol (ISAKMP) and the Oakley and Skeme key exchange methods. ISAKMP defines the message format, the mechanics of a key-exchange protocol, and the negotiation process to build an SA for IPsec. ISAKMP does not define how keys are managed or shared between the two IPsec peers. Oakley and Skeme have five defined key groups. Of these groups, Cisco routers support Group 1 (768-bit key), Group 2 (1024-bit key), and Group 5 (1536-bit key).
IKE combines these protocols to build secure IPsec connections between devices. It establishes SAs that are mutually agreeable to each peer. Each peer must have identical ISAKMP and IPsec parameters to establish an operational and secure VPN. Note that the terms ISAKMP and IKE are commonly used by industry people to refer to IKE.
An alternative to using IKE is to manually configure all parameters required to establish a secure IPsec connection. This process is impractical because it does not scale.
Phase 1 - Two IPsec peers perform the initial negotiation of SAs. The basic purpose of Phase 1 is to negotiate IKE policy sets, authenticate the peers, and set up a secure channel between the peers. It can be implemented in main mode (longer, initial contact) or aggressive mode (after initial contact).
Phase 2 - SAs are negotiated by the IKE process ISAKMP on behalf of IPsec. It can be negotiated in quick mode.
Общая схема выглядит вот так, но ОНА ТУПАЯ
-------------------------------------------------------------------------------------------
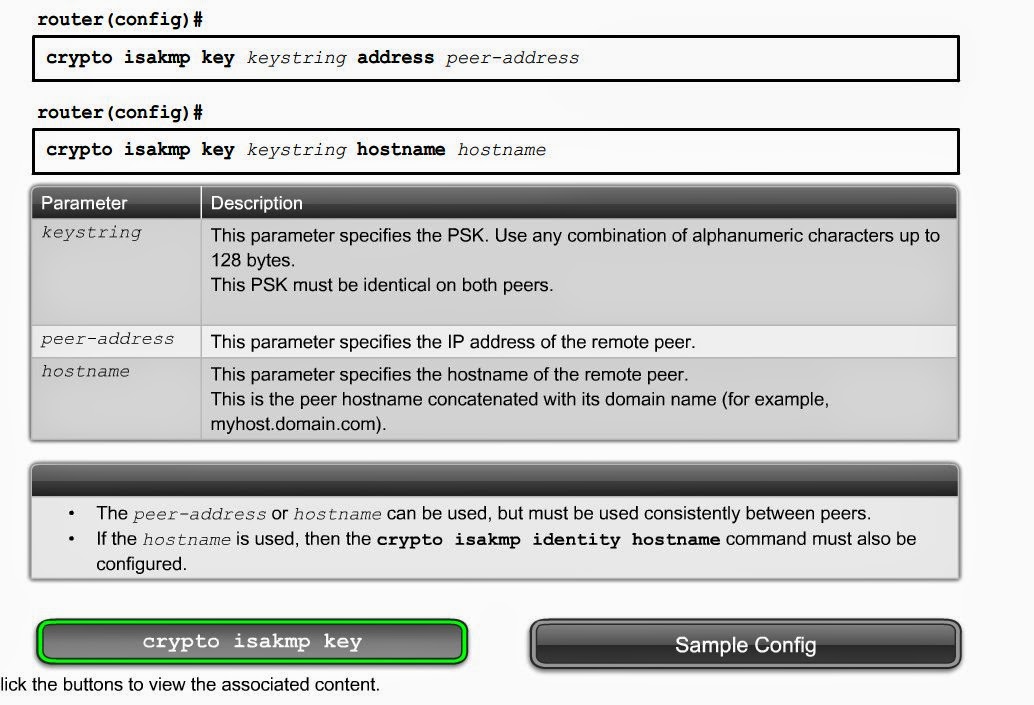
Непосредственно конфигурация по делу











































Комментариев нет:
Отправить комментарий